Description of problem:
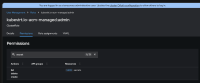
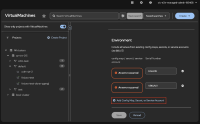
kubevirt.io-acm-managed:admin role is missing 'get' for 'secret'. As a result, rbac user is not being able to see/add new secrets to the VM.
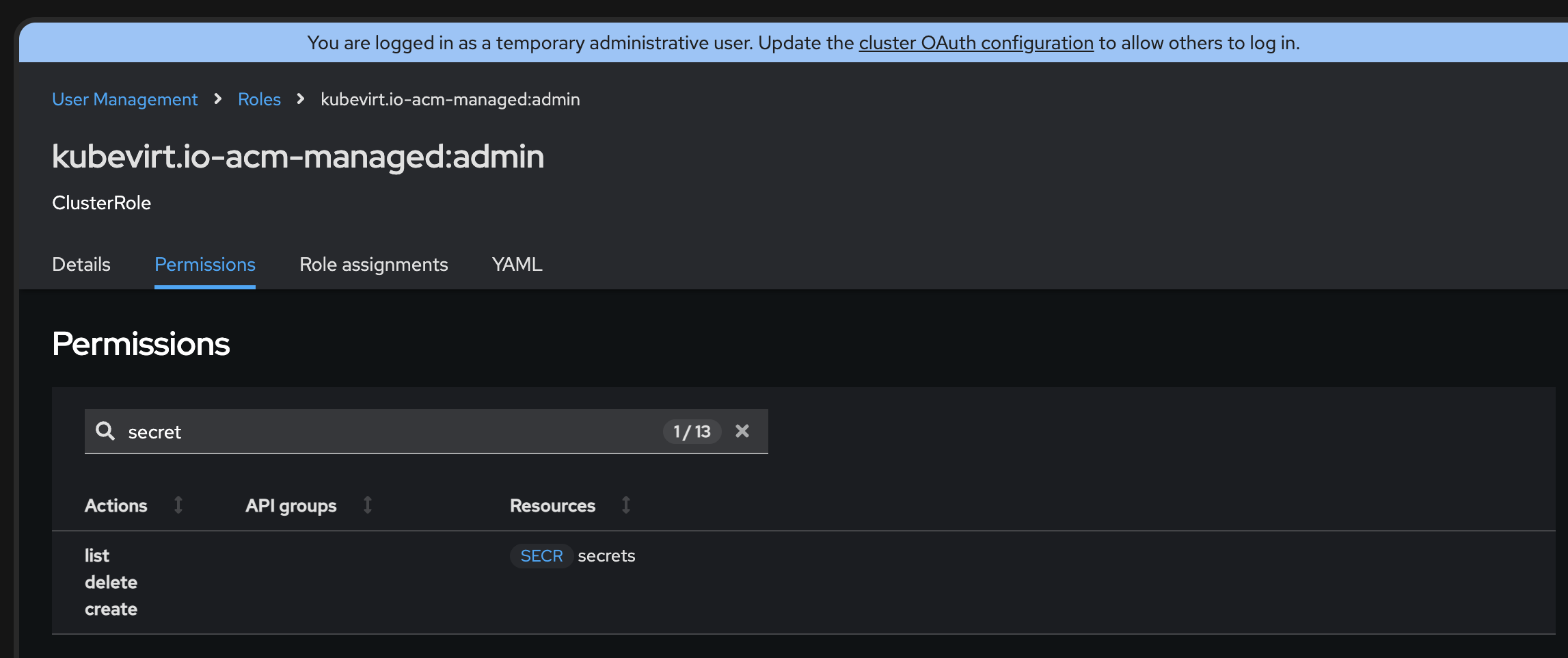
Verified by patching the permissions for this role -
shafi@ashafi-mac clc-ui % oc get clusterrole kubevirt.io-acm-managed:admin -o json | jq '.rules[] | select(.resources[]? == "secrets")' { "apiGroups": [ "" ], "resources": [ "secrets" ], "verbs": [ "list", "delete", "create", "get" ] }
Once added, user can add/see the secrets. However, the permission reverts back and loses the 'get' permissions after ~20s (Some controller reconciling it?) -
ashafi@ashafi-mac clc-ui % oc get clusterrole kubevirt.io-acm-managed:admin -o json | jq '.rules[] | select(.resources[]? == "secrets")' { "apiGroups": [ "" ], "resources": [ "secrets" ], "verbs": [ "list", "delete", "create" ] }
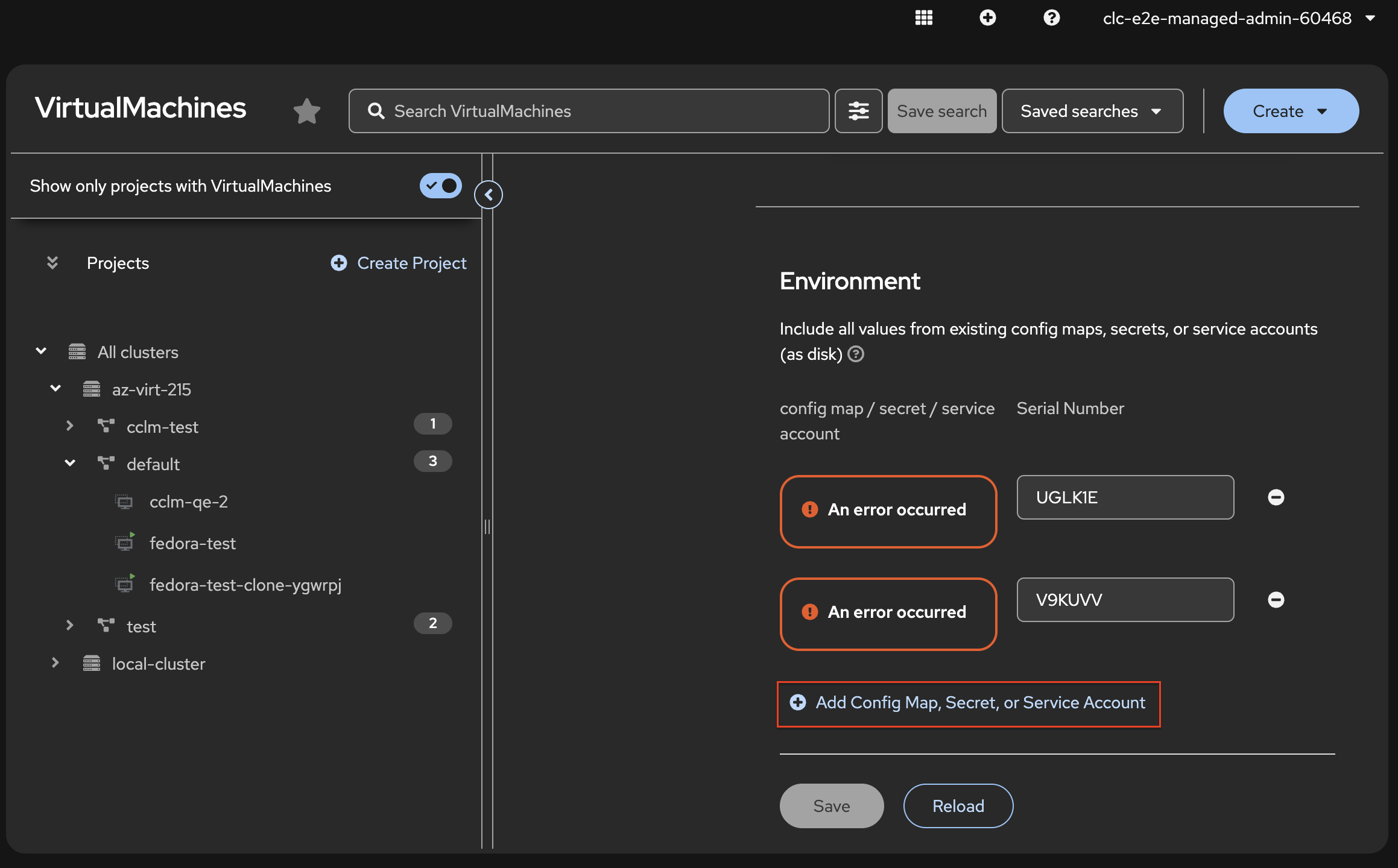
After, the user fails to see or add any secrets (or others on this section).
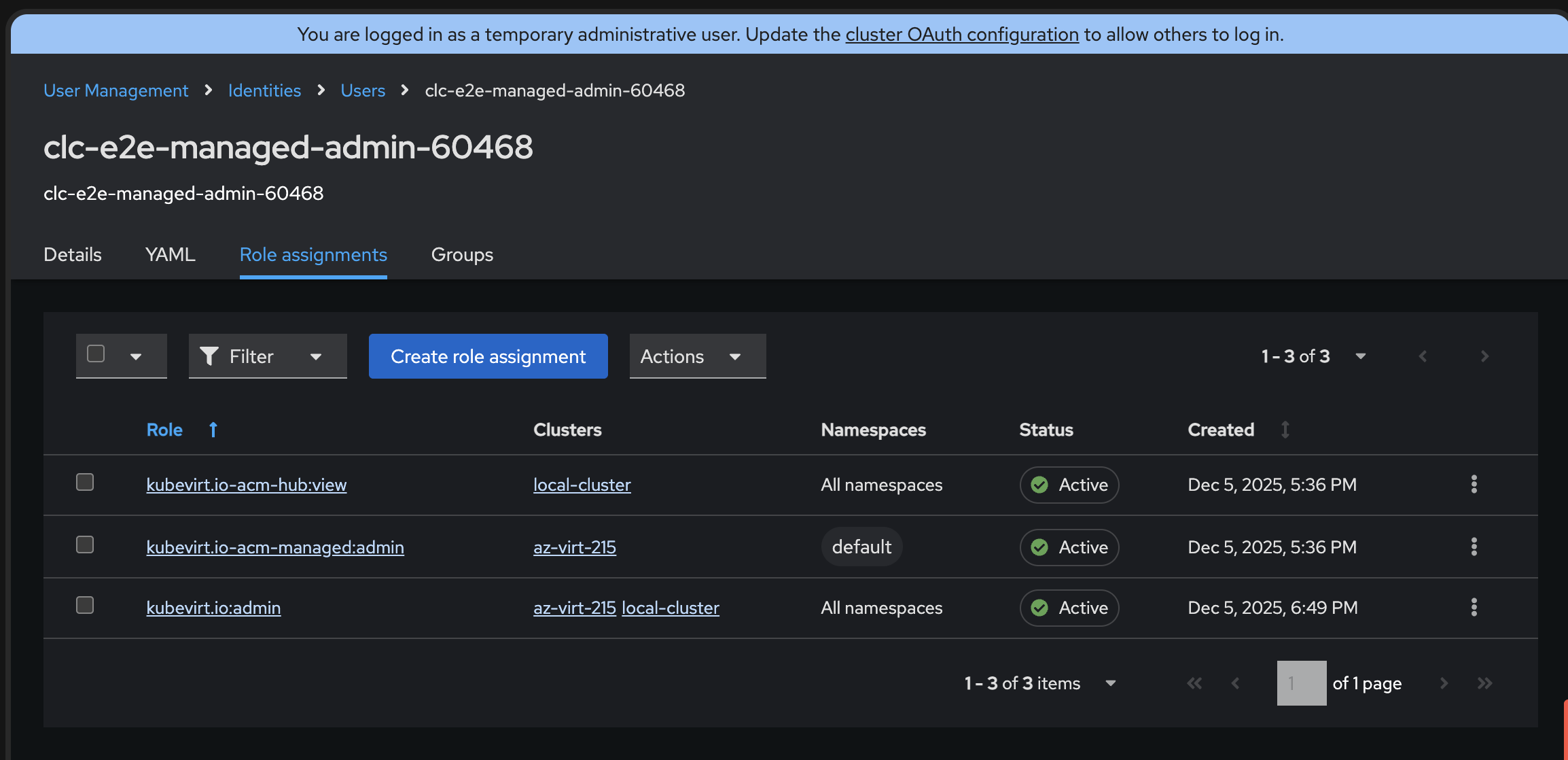
User -
Version-Release number of selected component (if applicable): ACM 2.15 RC, CNV v4.21.0.rhel9-31 (candidate)
How reproducible: Always
Potential fix: Add 'get' under here: https://github.com/stolostron/multiclusterhub-operator/blob/44e0166fd79e952b3dd355c7a2e7f20eda85c4f1/pkg/templates/charts/toggle/fine-grained-rbac/templates/acm-roles-addontemplate.yaml#L29
- is related to
-
ACM-26301 ACM Roles - Finalize
-
- Closed
-
-
ACM-26280 VM (on spoke) Configuration tab fails to configure for secrets/configmaps on Fleet UI
-
- Closed
-
- relates to
-
CNV-79601 Fleet Virtualization UI - Mounting config map / secret / service account as disk requires permissions to all 3 resources
-
- New
-