-
Bug
-
Resolution: Done
-
Major
-
ACM 2.14.0
-
Product / Portfolio Work
-
False
-
-
False
-
-
-
Search Sprint 2025-12
-
Critical
-
Approved
-
None
Description of problem:
When testing VM RBAC e2e, we found this bug. When logging into the ACM hub with an IDP user who is assigned kubevirt.io:admin permissions to some VMs through ClusterPermission, the Delete VirtualMachine operation is not allowed. It gives this error:
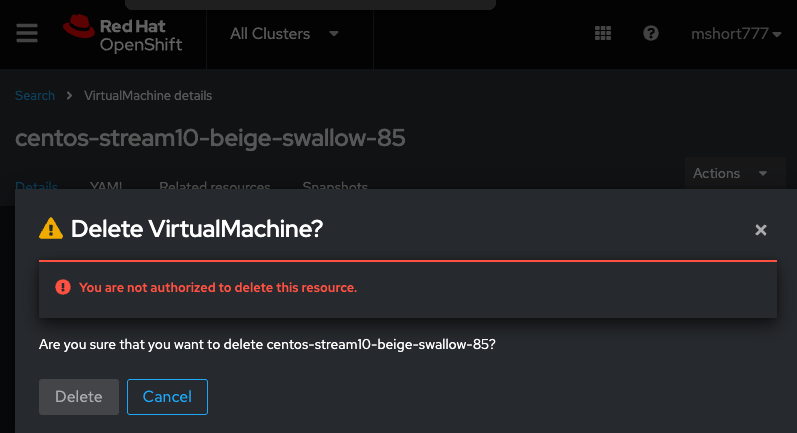
(Delete is greyed out)
The workaround is to add these permissions to the user trying to delete a VM on the hub cluster:
--- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: acm-kubevirt-rbac-required rules: - apiGroups: ["kubevirt.io"] resources: ["virtualmachines"] verbs: ["delete"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: acm-kubevirt-rbac-required roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: acm-kubevirt-rbac-required subjects: - apiGroup: rbac.authorization.k8s.io kind: User name: mshort777
The fact that we have to add permissions on the hub cluster here seems to point to this being a UI bug. Deleting a VM should not require any permissions on the hub cluster because permissions are handled by ClusterPermission and should only be needed on the managed cluster.
There is a 2nd part to this bug. After adding the above permissions, we get this new error when trying to delete a VM:
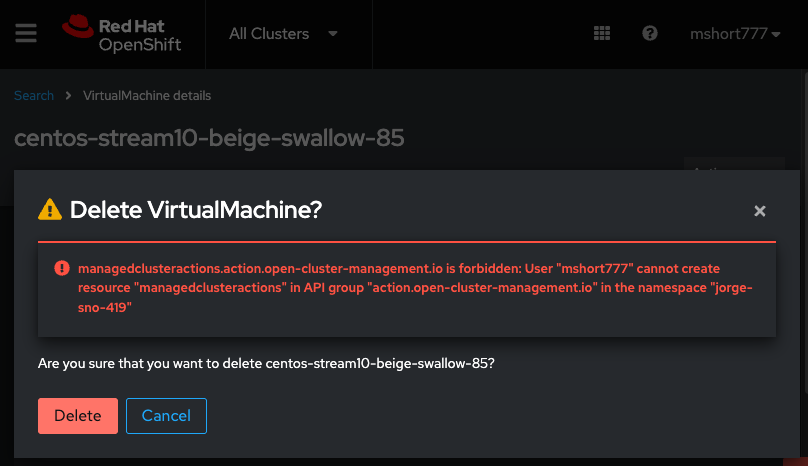
From talking to jpadilla@redhat.com , my understanding is that the proxy/impersonation should be used here rather than managedclusteractions.
Adding these permissions on the hub cluster to the user logging in resolves the issues. We are using it as a workaround to this issue for the 2.14 tech preview:
(add this section to the above yaml) - apiGroups: ["action.open-cluster-management.io"] resources: ["managedclusteractions"] verbs: ["create", "get", "delete"]
Version-Release number of selected component (if applicable):
How reproducible:
Every time.
Steps to Reproduce:
1. Set up Github IDP
(follow instructions here: ACM-21454)
2. Create ClusterPermission
apiVersion: rbac.open-cluster-management.io/v1alpha1 kind: ClusterPermission metadata: name: jorge-dev-bm-clustervirtadmin namespace: jorge-dev-bm spec: clusterRoleBinding: roleRef: name: kubevirt.io:admin apiGroup: rbac.authorization.k8s.io kind: ClusterRole subjects: - name: mshort777 apiGroup: rbac.authorization.k8s.io kind: User
(change name, namespace, and subject name accordingly)
3. Log into hub cluster, select VM, and try to delete.
Actual results:
VM is unable to be deleted.
Expected results:
VM should be deleted.
Additional info:
- is duplicated by
-
ACM-21458 Delete VM snapshot not working due to missing permission which should not be needed
-
- Closed
-