-
Bug
-
Resolution: Done
-
Major
-
ACM 2.14.0
-
Product / Portfolio Work
-
False
-
-
False
-
-
-
Search Sprint 2025-12
-
Critical
-
None
Description of problem:
When testing VM RBAC e2e, we found this bug. When logging into the ACM hub with an IDP user who is assigned permissions to some VMs through ClusterPermission, the VM details page does not load. It gives this error:
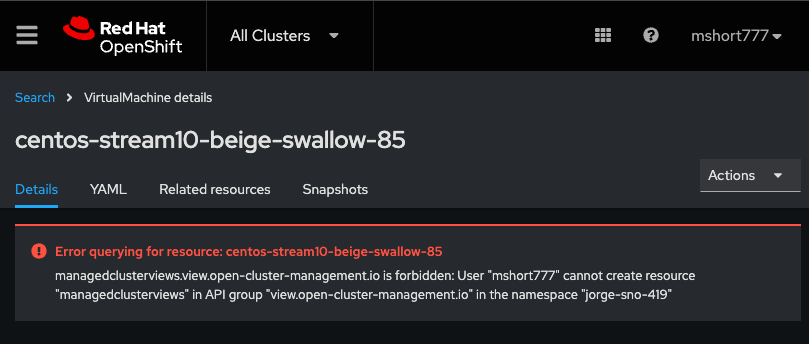
This also affects taking VM snapshots:
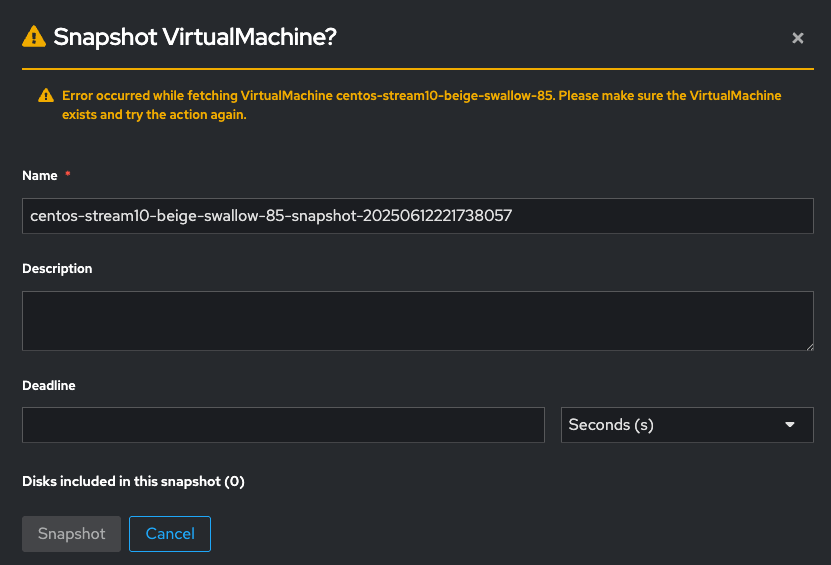
From talking to jpadilla@redhat.com , my understanding is that the proxy/impersonation should be used here rather than managedclusterviews.
Adding these permissions on the hub cluster to the user logging in resolves the issues. We are using it as a workaround to this issue for the 2.14 tech preview:
--- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: acm-kubevirt-rbac-required rules: - apiGroups: ["view.open-cluster-management.io"] resources: ["managedclusterviews"] verbs: ["create", "get", "delete"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: acm-kubevirt-rbac-required roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: acm-kubevirt-rbac-required subjects: - apiGroup: rbac.authorization.k8s.io kind: User name: mshort777
.Version-Release number of selected component (if applicable):
How reproducible:
Every time.
Steps to Reproduce:
1. Set up Github IDP
Set up github IDP: 1. create github org 2. org settings - Developer settings - OAuth Apps - New OAuth app Application name: any name Homepage URL: run command to get: oc get routes oauth-openshift -n openshift-authentication example: https://oauth-openshift.apps.vboulos-hcp-srch.dev09.red-chesterfield.com Authorization callback URL: <homepageurl>/oauth2callback/github example: https://oauth-openshift.apps.vboulos-hcp-srch.dev09.red-chesterfield.com/oauth2callback/github 3. click button to Generate a new client secret 4. create secret: oc create secret generic <secret_name> --from-literal=clientSecret=<secret> -n openshift-config example: oc create secret generic github-idp-e2e-test --from-literal=clientSecret=<client-secret-from-previous-step> -n openshift-config 5. apply oauth yaml: (change clientID to match actual github oauth client ID) (change organizations to match actual github organization) apiVersion: config.openshift.io/v1 kind: OAuth metadata: name: cluster spec: identityProviders: - name: github mappingMethod: claim type: GitHub github: clientID: Ov23liUkiIqisdooxqdk clientSecret: name: github-idp-e2e-test organizations: - acm-cluster-virtualization-team-test 6. perform above steps on hub AND spoke cluster/s. Each hub and managed cluster needs to have a seperate github oauth app created
2. Create ClusterPermission
apiVersion: rbac.open-cluster-management.io/v1alpha1 kind: ClusterPermission metadata: name: jorge-dev-bm-clustervirtadmin namespace: jorge-dev-bm spec: clusterRoleBinding: roleRef: name: kubevirt.io:admin apiGroup: rbac.authorization.k8s.io kind: ClusterRole subjects: - name: mshort777 apiGroup: rbac.authorization.k8s.io kind: User
(change name, namespace, and subject name accordingly)
3. Log into hub cluster and click on any VM to open the VM details page, you will get the first error shown. Try to create a snapshot and you will get the 2nd error.
Actual results:
Forbidden error is shown.
Expected results:
Should show VM details page.