-
Sub-task
-
Resolution: Obsolete
-
Major
-
None
-
Product / Portfolio Work
-
False
-
-
False
-
-
-
VMMgmt - Train-31
The tech preview implementation of the Access Control page supports changing the role on the EDIT page:
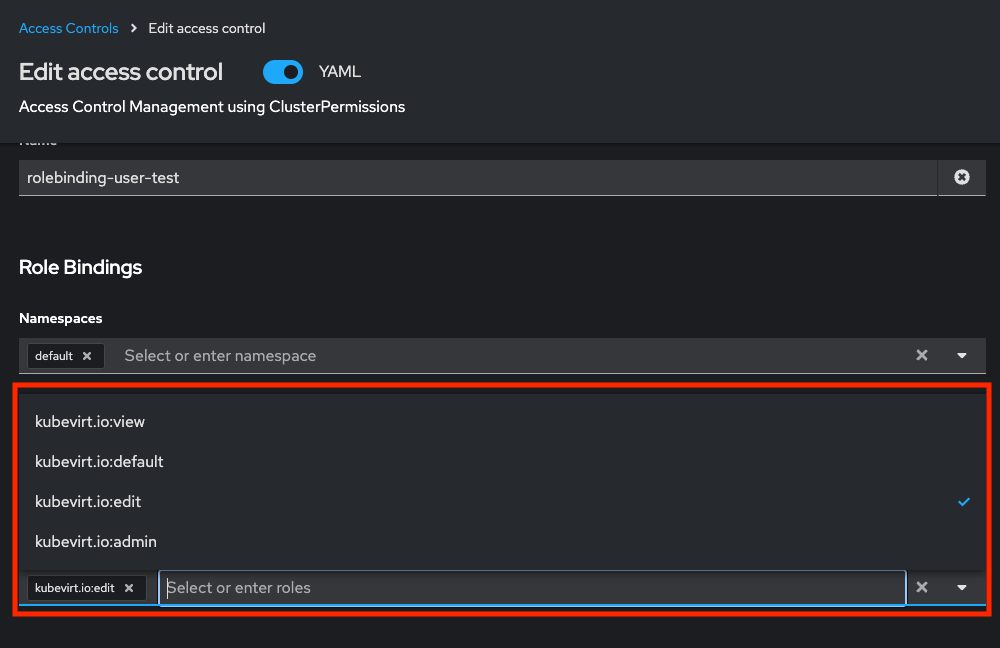
However this is not supported by ManifestWork. This error can be seen in the ManifestWork output:
ubuntu@ubuntu2404:~/UbuntuSync/ACM/clusterpermissionyaml$ kubectl -n local-cluster get ManifestWork rolebinding-user-test-675f2 -o yaml apiVersion: work.open-cluster-management.io/v1 kind: ManifestWork metadata: creationTimestamp: "2025-06-02T21:40:30Z" finalizers: - cluster.open-cluster-management.io/manifest-work-cleanup generation: 7 name: rolebinding-user-test-675f2 namespace: local-cluster ownerReferences: - apiVersion: rbac.open-cluster-management.io/v1alpha1 blockOwnerDeletion: true controller: true kind: ClusterPermission name: rolebinding-user-test uid: 675f26e3-bdc1-4bac-a701-243c5e7ab738 resourceVersion: "7685278" uid: ae8fc912-8e64-4bec-a6d3-f7cd9ebe4cad spec: workload: manifests: - apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: rolebinding-user-test namespace: default roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: kubevirt.io:edit subjects: - apiGroup: rbac.authorization.k8s.io kind: User name: Matt status: conditions: - lastTransitionTime: "2025-06-02T21:45:18Z" message: Failed to apply manifest work observedGeneration: 7 reason: AppliedManifestWorkFailed status: "False" type: Applied - lastTransitionTime: "2025-06-02T21:40:30Z" message: All resources are available observedGeneration: 7 reason: ResourcesAvailable status: "True" type: Available resourceStatus: manifests: - conditions: - lastTransitionTime: "2025-06-02T21:45:18Z" message: 'Failed to apply manifest: RoleBinding.rbac.authorization.k8s.io "rolebinding-user-test" is invalid: roleRef: Invalid value: rbac.RoleRef{APIGroup:"rbac.authorization.k8s.io", Kind:"ClusterRole", Name:"kubevirt.io:edit"}: cannot change roleRef' reason: AppliedManifestFailed status: "False" type: Applied - lastTransitionTime: "2025-06-02T21:44:13Z" message: Resource is available reason: ResourceAvailable status: "True" type: Available - lastTransitionTime: "2025-06-02T21:44:13Z" message: "" reason: NoStatusFeedbackSynced status: "True" type: StatusFeedbackSynced resourceMeta: group: rbac.authorization.k8s.io kind: RoleBinding name: rolebinding-user-test namespace: default ordinal: 0 resource: rolebindings version: v1 statusFeedback: {}
Main error is "cannot change roleRef". Therefor we need to decide how to handle this, whether to figure out how to allow changing or to just block this option from being changeable after ClusterPermission creation.
This task has some things in common with ACM-21184. If we added a name to each rolebinding, then we can make changes to the role if we change the name at the same time. For example if we start with this:
apiVersion: rbac.open-cluster-management.io/v1alpha1
kind: ClusterPermission
metadata:
name: rolebindings-test
namespace: local-cluster
spec:
roleBindings:
- name: test1
namespace: default
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: role1
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: user1
We can change the role if we also change the rolebinding name at the same time like this:
apiVersion: rbac.open-cluster-management.io/v1alpha1
kind: ClusterPermission
metadata:
name: rolebindings-test
namespace: local-cluster
spec:
roleBindings:
- name: test2
namespace: default
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: role2
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: user1
The same thing works for clusterrolebinding. Start with this:
apiVersion: rbac.open-cluster-management.io/v1alpha1 kind: ClusterPermission metadata: name: clusterrolebinding-test namespace: local-cluster spec: clusterRoleBinding: name: crb-1 roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: role1 subjects: - apiGroup: rbac.authorization.k8s.io kind: User name: user1
When changing clusterrole name, if you change clusterrole and clusterrolebinding names at the same time, it is accepted and changes successfully:
apiVersion: rbac.open-cluster-management.io/v1alpha1 kind: ClusterPermission metadata: name: clusterrolebinding-test namespace: local-cluster spec: clusterRoleBinding: name: crb-2 roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: role2 subjects: - apiGroup: rbac.authorization.k8s.io kind: User name: user1
- is related to
-
ACM-21184 Bug Fix for RBAC for VMs - Creation of multiple rolebindings fails
-
- Resolved
-