-
Feature Request
-
Resolution: Done
-
Normal
-
2.3
-
False
-
False
Description
Customer is requesting workflow described in ticket as an RFE.
Steps to Reproduce
General process:
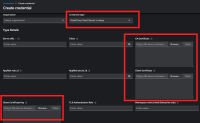
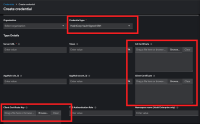
Configuration needed:
- Technical account to be used
- URL for Hashivault
- Owner name in certificate
- Client certificate and key
- Technical account for which the password is to be retrieved
3 steps: - With certificate, name space, account name, get access temporary token
- With temporary token, get path to secret for the technical account; may have several steps to get to the secret
- With temporary token, get secret for the technical account
Transcript (curl calls, secrets hidden):
#============================================================================
#./hashi-chk.pl: running hashicorp checks on AT1111
#------------------------------------------------------------------------------
#------------------------------------------------------------------------------
- getting tokens
-
- get token for runtime account FA11111
/usr/bin/curl \
--request POST \
--cert ./cert/FA11111.pem \
--key ./cert/FA11111.key \
--data '{"name":"cert_fa11111"}' \
-H "X-Vault-Namespace: AT1111" \
https://vault.eu.eva.ubs.net/v1/auth/cert/login
{"request_id":"f4daa1f6-6669-85e7-6f6a-b9845e4c5aa8","lease_id":"","renewable":false,"lease_duration":0,"data":null,"wrap_info":null,"warnings":null,"auth":{"client_token":"XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX","accessor":"WmGrJLjR6AVRNzwYTF0k7V45.LRNKt","policies":["default","runtimeread"],"token_policies":["default","runtimeread"],"metadata": {"authority_key_id":"7f:b1:5e:e5:bf:3d:a1:59:43:ce:a6:4e:14:90:08:2a:1b:23:6b:b1","cert_name":"cert_fa11111","common_name":"FA11111","serial_number":"1003533744341219157921498326779946632709447242","subject_key_id":"a4:ee:63:62:e0:3d:52:bf:94:25:f5:7f:20:9e:d7:65:3a:0e:ee:79"},"lease_duration":1800,"renewable":true,"entity_id":"ac3083bf-f1be-b9a9-ded6-77221e779990","token_type":"service","orphan":true}}
>> success: client_token for FA11111, runtime: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
- get token for runtime account FA11111
#------------------------------------------------------------------------------
- list secrets
-
- list secrets AT1111 using the token for runtime account FA11111 of XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
/usr/bin/curl \
--request GET \
-H "X-Vault-Token: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX" \
-H "X-Vault-Namespace: AT1111" \
https://vault.eu.eva.ubs.net/v1/secret/metadata/runtime?list=true
!!!secrets: :18cd3b627c07ba6401309ba46009e522d88832b0eff01395877c8b7dc8650193:, @secrets: :18cd3b627c07ba6401309ba46009e522d88832b0eff01395877c8b7dc8650193: {"request_id":"62d8be1d-7ab3-09f8-c89e-b4cfcb7ed8f1","lease_id":"","renewable":false,"lease_duration":0,"data":\{"keys":["18cd3b627c07ba6401309ba46009e522d88832b0eff01395877c8b7dc8650193/"]},"wrap_info":null,"warnings":null,"auth":null}
>> success: secret listing for path runtime: 18cd3b627c07ba6401309ba46009e522d88832b0eff01395877c8b7dc8650193
- list secrets AT1111 using the token for runtime account FA11111 of XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
-
- list secrets AT1111 using the token for runtime account FA11111 of XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
/usr/bin/curl \
--request GET \
-H "X-Vault-Token: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX" \
-H "X-Vault-Namespace: AT1111" \
https://vault.eu.eva.ubs.net/v1/secret/metadata/runtime/18cd3b627c07ba6401309ba46009e522d88832b0eff01395877c8b7dc8650193?list=true
!!!secrets: :SSO_SAMPLE,sso_other:, @secrets: :SSO_SAMPLE sso_other: {"request_id":"1bce8489-5674-8ed6-457b-63090712df4d","lease_id":"","renewable":false,"lease_duration":0,"data":\{"keys":["SSO_SAMPLE","sso_other"]},"wrap_info":null,"warnings":null,"auth":null}
>> success: secret listing for path runtime/18cd3b627c07ba6401309ba46009e522d88832b0eff01395877c8b7dc8650193: SSO_SAMPLE sso_other
- list secrets AT1111 using the token for runtime account FA11111 of XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
#------------------------------------------------------------------------------
- get npta passwords
-
- get password for runtime account SSO_SAMPLE using the token for runtime account FA11111: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
/usr/bin/curl \
--request GET \
-H "X-Vault-Token: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX" \
-H "X-Vault-Namespace: AT1111" \
https://vault.eu.eva.ubs.net/v1/secret/data/runtime/18cd3b627c07ba6401309ba46009e522d88832b0eff01395877c8b7dc8650193/SSO_SAMPLE
{"request_id":"74281b67-0005-bb23-51c5-fc5f84244bc0","lease_id":"","renewable":false,"lease_duration":0,"data":{"data": {"password":"XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX"},"metadata":{"created_time":"2021-05-14T10:49:24.394741728Z","deletion_time":"","destroyed":false,"version":2}},"wrap_info":null,"warnings":null,"auth":null}
>> success: got password: XXXXXXXXXXXXXXXXXXXX, account: SSO_SAMPLE, type: runtime, created: 2021-05-14T10:49:24.394741728Z, version: 2, retrieved by FA11111
- get password for runtime account SSO_SAMPLE using the token for runtime account FA11111: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
#==============================================================================
-
-
-
-
-
-
- results summary #######
SWCI: AT1111, environment: prod, runtime vault account FA11111, deploy vault account FA15763
accounts checked: runtime: SSO_SAMPLE, runtime: sso_other, deploy: sso_otherd
- results summary #######
-
-
-
-
-
success: client_token for FA11111, runtime: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
success: secret listing for path runtime: 18cd3b627c07ba6401309ba46009e522d88832b0eff01395877c8b7dc8650193
success: secret listing for path runtime/18cd3b627c07ba6401309ba46009e522d88832b0eff01395877c8b7dc8650193: SSO_SAMPLE sso_other
success: got password: XXXXXXXXXXXXXXXXXXXX, account: SSO_SAMPLE, type: runtime, created: 2021-05-14T10:49:24.394741728Z, version: 2, retrieved by FA11111
#------------------------------------------------------------------------------
#./hashi-chk.pl: completed hashicorp checks on AT1111
#============================================================================
Expected Behavior
Request secrets from Hashicorp Vault using client certificate