-
Bug
-
Resolution: Done
-
Major
-
netobserv-1.2
-
False
-
None
-
False
-
-
-
-
NetObserv - Sprint 234, NetObserv - Sprint 235, NetObserv - Sprint 236
-
Critical
- Create a htpasswd IDP with users such as "testuser-0" etc.
- Add "testuser-0" to cluster-admin or cluster-admins user group as:
oc adm policy add-cluster-role-to-user cluster-admin testuser-0
- Login using testuser-0
- Deploy latest Downstream operator and 0-click loki , create flowcollector in netobserv NS with authToken: Disabled.
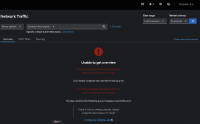
- In Web console, navigate to Netflow traffic page, I am seeing queries are Unauthorized when logged in as testuser-0
I verified users have cluster-admin role bindings, I tried assigning "cluster-admin" and "cluster-admins" role to the testuser-0 and also creating separate group and added testuser to that group and added cluster-admin role to the group but no luck, for e.g.:
oc adm groups new mylocaladmins oc adm groups add-users mylocaladmins testuser-0 oc adm policy add-cluster-role-to-group cluster-admin mylocaladmins
in console plugin logs, I see:
time="2023-03-31T18:03:55Z" level=debug msg="Checking auth: token found" module=handler.auth time="2023-03-31T18:03:55Z" level=debug msg="Checking authenticated user" module=handler.auth time="2023-03-31T18:03:55Z" level=debug msg="Checking auth: token found" module=handler.auth 2023/03/31 18:03:55 http: TLS handshake error from 10.129.0.86:45846: EOF time="2023-03-31T18:03:55Z" level=debug msg="Checking authenticated user" module=handler.auth time="2023-03-31T18:03:55Z" level=debug msg="Checking auth: token found" module=handler.auth time="2023-03-31T18:04:09Z" level=debug msg="Checking authenticated user" module=handler.auth time="2023-03-31T18:04:09Z" level=debug msg="Checking auth: token found" module=handler.auth time="2023-03-31T18:04:09Z" level=debug msg="Checking authenticated user" module=handler.auth
- links to
- mentioned on
(1 links to, 3 mentioned on)
Since the problem described in this issue should be resolved in a recent advisory, it has been closed.
For information on the advisory (Important: Network observability 1.3.0 for Openshift), and where to find the updated files, follow the link below.
If the solution does not work for you, open a new bug report.
https://access.redhat.com/errata/RHSA-2023:3905